Social Engineering & Phishing Simulation Services

Can your employees defend against an attack?
CSA can provide the information and resources to help transform your employees into your best defence against cyber aggression, which is increasingly targeting behaviours and not just code.
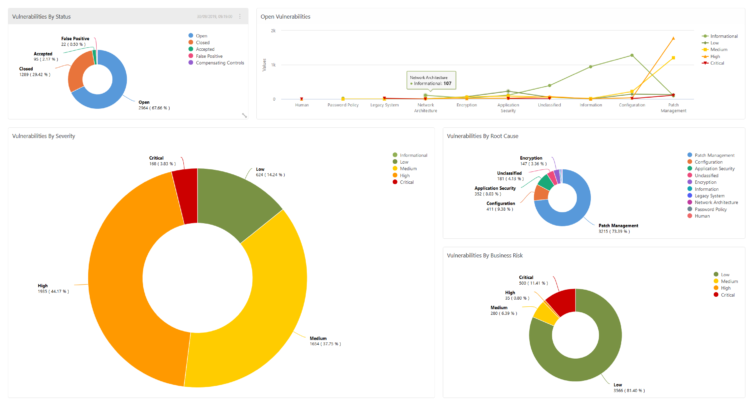
Gain a greater understanding of your security posture
The difference between CSA and other cyber-security service vendors is that once any one of the services below has been implemented the findings are delivered via the CSA Cyber platform for your users to review, meaning you can manage your remediation process effectively.

Social Engineering Services
CSA's experts will attempt to coerce employees to negate security processes through the use of various social techniques (phishing, spear phishing, whaling, voice or mobile messaging or physical on-site social engineering) in the attempt to gain unauthorised access or theft of sensitive data.

Ransomware Simulator
Uses advanced techniques to bypass existing spam filters and antivirus technologies to deliver a “real-life”, yet harmless, cyber-attack ransomware simulation. Through this you will identify which staff opened emails, clicked, and downloaded the malicious files – even those that attempted to pay the ransom. See what files were held to ransom, the reporting time frame and technical data on how filtering was bypassed.

Phishing Simulator
CSA provide custom and targeted phishing engagement campaigns. Our team can target individuals (spear-phishing) or the wider organisation through initial reconnaissance to provide a real-world demonstration of how attackers can obtain staff data. CSA's team then use real-world examples of successful phishing campaigns and bespoke scenarios to target your staff’s security awareness and incident handling process. Our experts can even craft these phishing simulations to bypass two-factor authentication mechanisms.

Physical Security Services
CSA can provide a thorough review of the physical security controls that are in place at your organisations offices. Dedicated and focused testing from our teams includes, but not limited to, CCTV placement and operational processes relating to monitoring, building and door access control systems (including RFID door control), door and window locking mechanisms, employee and visitor identification solutions.
Contact Us
Would you like to talk to us and find out more about our services?
